Cambodia E-Visa
Cambodia Is Changing
I Am The First
Making It On The TOP Ranking
I am the one who making the official Cambodia E-Visa on the top ranking of https://www.youtube.com/ and http://www.slideshare.net/ website.
Cambodia E-Visa system is spreading over the world, people is more easier to get it to the Kingdom of Cambodia because it saves cost and time.
I am the first to make E-Visa to be exposed on WTM (world trade magazine) publication as well as ABTA & ASTA destination guide book for the next coming year 2013.
And furthermore, I make Cambodia E-Visa information to be known and found by many social media including blogging, linkedin, facebook and twitter.
People are amazing when they see E-visa logo on those social media and particularly it has made their travel more comfortable. (More testimonial http://www.mfaic.gov.kh/evisa/Testimonial.aspx)
By: Han4U
Tuesday, July 31, 2012
10 Most Successful Businessmen
By: Mason Kaho
Break Studios Contributing Writer
A list of the ten most successful businessmen of all time includes some
of history's most industrious workers and innovative entrepreneurs. In
most cases, these men invented entire industries and changed the course
of history.
Reference: http://www.mademan.com/mm/10-most-successful-businessmen.html
-
John D. Rockefeller. Rockefeller is the richest man
of all time when adjusted for inflation and is certainly one of the ten
most successful businessmen. He created Standard Oil and completely
monopolized the oil industry, controlling every level of production from
start to finish.
-
Henry Ford. Ford created the Ford Motor Company and
essentially, the automobile industry. His developments changed the way
factories ran, the way society operated and the face of the country. His
company remains a major world force today.
-
Bill Gates. Gates became one of the ten most
successful businessmen of all time in the 1980’s when the software he
developed—Microsoft—took over the computing world. Nearly all computers
run Microsoft, and Gates is a major player in world economics.
-
Thomas Edison. Edison not only invented an item
nearly every person in the world uses everyday, the light bulb, he also
was the holder of over 1,000 patents at the time of his death. A symbol
of innovation, persistence and entrepreneurship, he is definitely one of
the ten most successful businessmen in history.
-
Soichiro Honda. Honda is certainly one of the ten
most successful businessmen in world history. He began making small
motorcycles in Japan in the mid 20th century and then moved into the
auto industry. His eponymous car company grew and gained a significant
foothold in the United States, opening the way for Japanese exports and
establishing a reputation for quality and reliability.
-
Steven Jobs. Jobs was co-founder of Apple, the
company that introduced a practical personal computer to the world, and
is one of the ten most successful businessmen in the country. He has
stayed at the helm of Apple, a company that continues to release
incredibly popular products.
-
Carlos Slim. Slim moved into the spot of “world’s
richest man” and obviously, one of the ten most successful businessmen
in the world. He has made his money in the telecom industry and is the
CEO of three companies.
-
Andrew Carnegie. Carnegie was an immigrant bobbin boy
in a factory as a child, and decades later, he became the biggest steel
magnate the world had ever seen. In his later years, he gave away a
large part of his vast fortune.
-
JP Morgan. Morgan, one of the ten most successful
businessmen ever, was one of a handful of corporate titans on the
American scene at the turn of the 20th century.
He was a banker and oversaw industrial consolidations in major
industries, such as steel and electronics. He stepped in during a
financial crisis and saved many New York banks in 1907.
- Michael Dell. Dell was an engineering whiz as a youngster and started a computer building business while in college. His company, today, is one of the biggest tech firms in the world, and most Americans spend their time online using a Dell computer.
Reference: http://www.mademan.com/mm/10-most-successful-businessmen.html
Sunday, July 29, 2012
Moustache Make A Different
Moustache is facial hair grown on the upper lip. It may or may not be accompanied by a type of beard, a facial hair style grown and cropped to cover most of the lower half of the face.
[Click on picture to see large size]
By: Han4U
[Click on picture to see large size]
By: Han4U
Friday, July 20, 2012
SQL Server – Configuring the Replication
Hello Folks,
I think you would have a brief idea of what the Replication is all about, and what are the types of Replication and the different agents equipped with the Replication.
Well, this article-post is mainly being focused on how to create a Publisher and Distributor, first time in the system.
Part 1: http://www.sqlservergeeks.com/articles/sql-server-bi/66/sql-server-%E2%80%93-configuring-the-replication-%E2%80%93-part-1
Part2: http://www.sqlservergeeks.com/articles/sql-server-bi/67/sql-server-%E2%80%93-configuring-the-replication-%E2%80%93-part-2
Part3: http://www.sqlservergeeks.com/articles/sql-server-bi/69/sql-server-%E2%80%93-configuring-the-replication-%E2%80%93-part-3
Reference: http://www.sqlservergeeks.com
Thursday, July 19, 2012
SQL SERVER 2008, how to add more tables in existing replication
To add more tables into article of existing publication, we have to create new snapshot of publication.
I have done it just now. It is very useful technique for whom that is as SQL Server 2008 developers want to do database replication.
Reference: http://www.sqlservercentral.com/Forums/Topic448781-146-1.aspx
By: Han4U
=> Right click on "New publication" and follow the steps.
I have done it just now. It is very useful technique for whom that is as SQL Server 2008 developers want to do database replication.
Reference: http://www.sqlservercentral.com/Forums/Topic448781-146-1.aspx
By: Han4U
Wednesday, July 18, 2012
Options to not replicate SQL Server DELETE commands
Problem
I have transactional replication configured in my production environment. The business team has requested that I do not replicate delete operations on certain articles. In this tip we look at a couple of options to not replicate DELETE commands.Solution
In some cases older data may be required on the subscriber, but deleted at the publisher. In order to meet this requirement we could use either of the options outlined below. Note, both options assume transactional replication is already configured between two databases.Option 1: Modifying Replication Settings
In this option we will use SSMS to make the changes, but this could be done using T-SQL commands as well.In SSMS go to Replication -> Local Publications and right click on your publication and select Properties. In the Publication Properties window click on 'Articles' and select the relevant article. Go to "Article Properties" and select "Set Properties of Highlighted Table Article" as shown below.
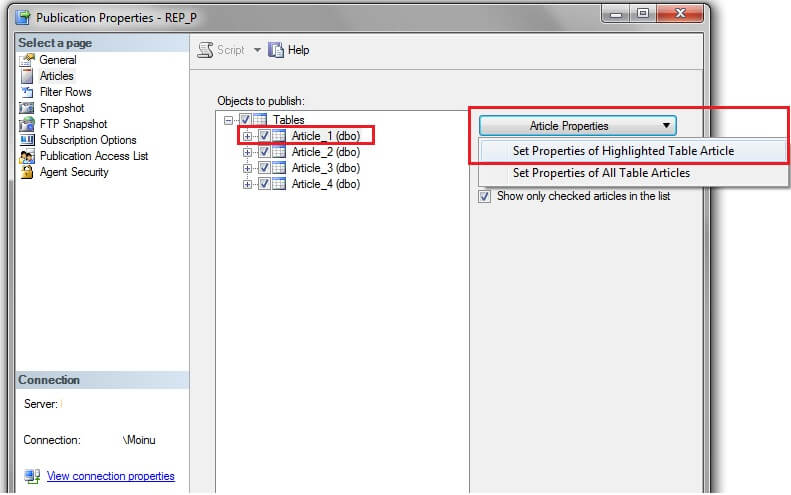
In the article properties window, change the "DELETE delivery format" to "Do not replicate DELETE statements".
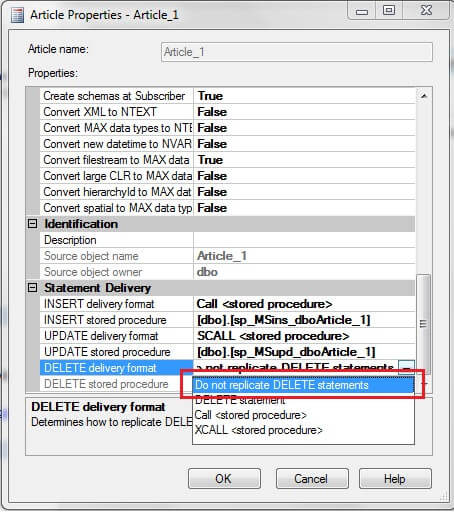
After the change click OK and you will see the below prompt. As the article property has been changed the subscriptions need to be reinitialized. Click "Mark for Reinitialization" which causes the snapshot to be applied to the subscriber.
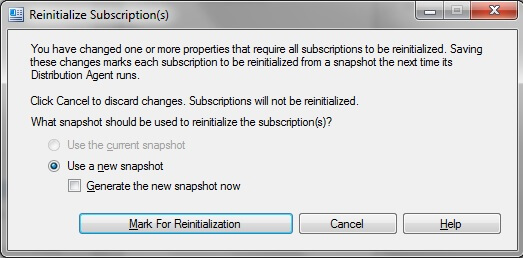
In SSSM, navigate to Replication and right click and select "Launch Replication Monitor" as shown below. Go to your publication and click View Details as shown below to see the snapshot progress.
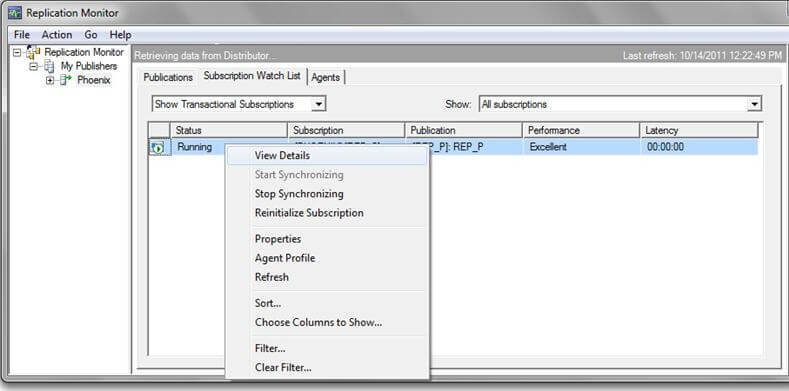
After clicking "View Details", you can see the details of the snapshot generation for the subscriber.
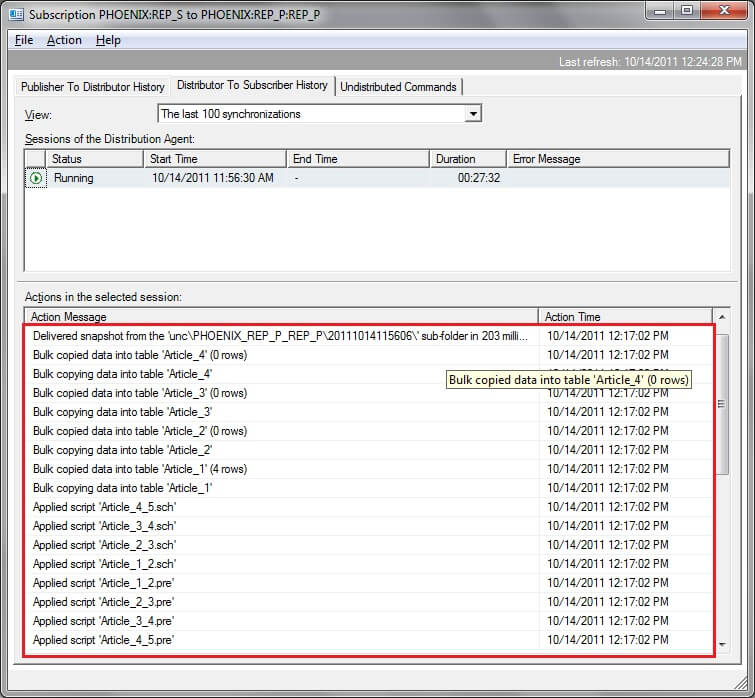
As you can see the entire snapshot is getting applied to the subscriber. This option must be used with caution as there may be cases where your subscriber database is used as an archive and may have more data than your publisher database. However, this depends on your environment and if your application is fine with getting the entire snapshot you could use this method. Also, for very large databases you may not want to reinitialize the entire snapshot either, so again use caution.
Once this change has been made and if there is a need to revert to replicating deletes, just perform similar steps as above to allow delete operations by calling the replication delete stored procedure at the subscriber. Call
Option 2 : Modifying the replication stored procedure in the subscriber database
For transactional replication, by default, stored procedures get created in the subscriber database for insert, update and delete operations. These could be viewed as shown in the screenshot below.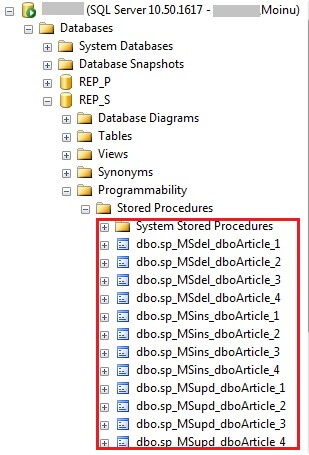
REP_S is the subscriber database and we could see the insert, update and delete stored procedures that were created for each subscribed article. In option (1), we need to be concerned about the snapshot getting applied when we modify the article property. However, in order to overcome this shortcoming, there were some discussions I came across on the internet to make the replication delete procedure in the subscriber database to just RETURN and not actually do the DELETE. This would ensure that the replication delete procedure in the subscriber database exits unconditionally even though it is called. As per books online, RETURN in T-SQL enables you to "Exit unconditionally from a query or procedure. RETURN is immediate and complete and can be used at any point to exit from a procedure, batch, or statement block. Statements that follow RETURN are not executed." (Source - http://msdn.microsoft.com/en-us/library/ms174998.aspx).
Using this concept, the delete procedure in the subscriber database could be modifed as shown. I have just added the RETURN statement right after the BEGIN, so the stored procedure exits immediately without doing the actual DELETE. With this approach, we need not worry about the snapshot getting applied again to the subscriber.
--Include RETURN statement in stored procedure and alter the stored procedure in the subscriber database
USE [REP_S]
GO
/****** Object: StoredProcedure [dbo].[sp_MSdel_dboArticle_1] Script Date: 10/14/2011 22:00:43 ******/
SET ANSI_NULLS ON
GO
SET QUOTED_IDENTIFIER ON
GO
ALTER procedure [dbo].[sp_MSdel_dboArticle_1] @pkc1 int
as
begin
RETURN
delete [dbo].[Article_1]
where [Col1] = @pkc1 if @@rowcount = 0
if @@microsoftversion>0x07320000
exec sp_MSreplraiserror 20598
end
GO
Summary
Both options could be tested easily with a simple publication of a single article and performing the sequence of steps as shown above. Also you should use Replication Monitor to see if there are any errors.Note: the above steps were performed using SQL Server 2008 R2.
Next Steps
- Consider testing this scenario through a simple transactional replication setup
- Refer to other related tips on replication to get familiar with the concepts
By: Mohammed Moinudheen
Mohammed is a SQL Server DBA with over 6 years experience managing production databases for a few Fortune 500 companies.
Reference: http://www.mssqltips.com/sqlservertip/2520/options-to-not-replicate-sql-server-delete-commands/
Tuesday, July 17, 2012
More Confident = More Money, Women, Love, Life, and Happiness
Have you always wanted to learn how to be confident, but just can’t
seem to get it right? Perhaps you are naturally shy, or have problems
speaking up in public situations. Maybe you can’t seem to stop second
guessing your decisions, and you allow others to dictate what you should
do. Or, you might just want to become more of a leader at work, or in
your personal life instead. Whatever your situation, you’ve likely tried
a number of different approaches, which have only given you mediocre
results. What is the answer, and how can you finally turn everything
around, and boost your confidence levels like never before?
The Problem!
Before you can discover how to be confident, you first need to uncover the primary problem. You see, most self-help systems and products only touch on the surface, by talking about the symptoms of low self-assurance. Rather than getting down to the heart of the matter, they work to correct issues which won’t give you lasting change. Ever heard the popular advice “Act confident and you’ll become confident”? It sounds like good advice on the surface, but when you dig deeper you find a fatal flaw. How do you act confident when you don’t even know what confidence looks like? Short answer – you don’t! You usually end up emulating someone who is arrogant, because they appear to have all the qualities of confidence you’re looking for…at least on the outside. Problem is, they’re not confident on the inside, and following them won’t make you any more confident.
What’s the Answer?
You must do a 180 degree turn, and dig out the root cause of your problems instead. If you commit to this process, then you will begin to see every area of your life begin to change! Rather than making minor improvements in only one specific issue, the bigger picture will start to get radically better. That means your financial situation can turn around in dramatic fashion, and you won’t have to work as hard to make things happen for you. You may even find yourself feeling truly happy for the first time in a long time! In your personal life, you may discover that you are attracting healthy, loving relationships easily – with no conscious effort on your part. Finally, without all of the negative emotions constantly holding you down, you may realize that you have more energy and passion than ever before. In short, your entire life could be turned upright once again, and you could begin living how you’ve always wanted!
How Does It Work?
If you want to know how to be confident, you probably realize that treating your symptoms simply won’t work. Yet, how can you uncover the root issue, which is causing all of your problems to grow and flourish? This process is much like a mystery, where you chart all of your issues, which will give you clues into your personal struggles. Yet, as you go through this journey, you will inevitably end up at only one conclusion. You see, everyone’s root issue is the same, whether they realize it or not! Having an inadequate self-image, will give rise to every other symptom you want to be rid of for good.
How Do You Change?
At this point you are probably asking, if this is true, how do you change your self-image for the better? The good news is, anyone can make a massive transformation in how they see themselves. Unfortunately, this task isn’t easy and many popular products for doing so, don’t work effectively. Methods like meditation, visualization and positive affirmation are inferior, because they require a high degree of self-discipline. In the majority of cases, people try them for a short time, and then they become frustrated and quit. Luckily, a new technology has recently been developed, which makes changing your self-image fast and easy.
Entrain Your Brain!
This revolutionary new technique is termed Brainwave Entrainment, and it is based upon the laws of physics. When two items are vibrating in close proximity, they tend to match each other’s vibrations perfectly. In fact, this is probably the reason certain musical rhythms and sounds produce emotional responses in people. As your brain is stimulated by beat, it comes into alignment and causes your brain activity to literally change! Using this information, sound engineers are able to create special tracks, which change how you think on an electrical level. For example, listening to Theta sound waves, seems to make learning easier. In contrast, Brainwave Entrainment which focuses upon your Alpha waves instead, may cause a more meditative state to arise.
The Morry Method.
Yet, while all of these benefits of Brainwave Entrainment are good, not all systems are of the same caliber. If you want to know how to be confident, then you need the right person to be your guide! Morry Zelcovitch is an excellent choice, as he used to be where you are now. He suffered from terrible depression, was accident prone and he couldn’t seem to stop talking. After finally getting fed up with his problems, he decided to do something about them. He stumbled upon Brainwave Entrainment, but the products he used only gave him temporary results. Yet, he knew that he was on the right track, and he only needed more learning to find the answer he was looking for.
To that end, Morry studied under the world’s top Brainwave Entrainment researcher David Siever, until he had fully mastered this technology. Then he created his own unique system, which finally resolved all of his issues! He was so relieved and grateful to get to the root of his problems, he decided to make this product available to everyone who needed to learn how to be confident.
Change Your Self-Image.
The product is called Quantum Confidence with the Morry Method, and it is one of a kind. You benefit from Morry’s unique expertise, and you can follow in his footsteps – to achieve the same results! If you are desperate to discover how to be confident, and you want to make a radical change in your life, then this system may be perfect for you. It doesn’t require any special skills, or a high level of dedication, as all you have to do is sit back and listen. So, why not do something to improve every area of your life today, and get your own copy now?
Reference: http://www.moreconfident.org/
The Problem!
Before you can discover how to be confident, you first need to uncover the primary problem. You see, most self-help systems and products only touch on the surface, by talking about the symptoms of low self-assurance. Rather than getting down to the heart of the matter, they work to correct issues which won’t give you lasting change. Ever heard the popular advice “Act confident and you’ll become confident”? It sounds like good advice on the surface, but when you dig deeper you find a fatal flaw. How do you act confident when you don’t even know what confidence looks like? Short answer – you don’t! You usually end up emulating someone who is arrogant, because they appear to have all the qualities of confidence you’re looking for…at least on the outside. Problem is, they’re not confident on the inside, and following them won’t make you any more confident.
What’s the Answer?
You must do a 180 degree turn, and dig out the root cause of your problems instead. If you commit to this process, then you will begin to see every area of your life begin to change! Rather than making minor improvements in only one specific issue, the bigger picture will start to get radically better. That means your financial situation can turn around in dramatic fashion, and you won’t have to work as hard to make things happen for you. You may even find yourself feeling truly happy for the first time in a long time! In your personal life, you may discover that you are attracting healthy, loving relationships easily – with no conscious effort on your part. Finally, without all of the negative emotions constantly holding you down, you may realize that you have more energy and passion than ever before. In short, your entire life could be turned upright once again, and you could begin living how you’ve always wanted!
How Does It Work?
If you want to know how to be confident, you probably realize that treating your symptoms simply won’t work. Yet, how can you uncover the root issue, which is causing all of your problems to grow and flourish? This process is much like a mystery, where you chart all of your issues, which will give you clues into your personal struggles. Yet, as you go through this journey, you will inevitably end up at only one conclusion. You see, everyone’s root issue is the same, whether they realize it or not! Having an inadequate self-image, will give rise to every other symptom you want to be rid of for good.
How Do You Change?
At this point you are probably asking, if this is true, how do you change your self-image for the better? The good news is, anyone can make a massive transformation in how they see themselves. Unfortunately, this task isn’t easy and many popular products for doing so, don’t work effectively. Methods like meditation, visualization and positive affirmation are inferior, because they require a high degree of self-discipline. In the majority of cases, people try them for a short time, and then they become frustrated and quit. Luckily, a new technology has recently been developed, which makes changing your self-image fast and easy.
Entrain Your Brain!
This revolutionary new technique is termed Brainwave Entrainment, and it is based upon the laws of physics. When two items are vibrating in close proximity, they tend to match each other’s vibrations perfectly. In fact, this is probably the reason certain musical rhythms and sounds produce emotional responses in people. As your brain is stimulated by beat, it comes into alignment and causes your brain activity to literally change! Using this information, sound engineers are able to create special tracks, which change how you think on an electrical level. For example, listening to Theta sound waves, seems to make learning easier. In contrast, Brainwave Entrainment which focuses upon your Alpha waves instead, may cause a more meditative state to arise.
The Morry Method.
Yet, while all of these benefits of Brainwave Entrainment are good, not all systems are of the same caliber. If you want to know how to be confident, then you need the right person to be your guide! Morry Zelcovitch is an excellent choice, as he used to be where you are now. He suffered from terrible depression, was accident prone and he couldn’t seem to stop talking. After finally getting fed up with his problems, he decided to do something about them. He stumbled upon Brainwave Entrainment, but the products he used only gave him temporary results. Yet, he knew that he was on the right track, and he only needed more learning to find the answer he was looking for.
To that end, Morry studied under the world’s top Brainwave Entrainment researcher David Siever, until he had fully mastered this technology. Then he created his own unique system, which finally resolved all of his issues! He was so relieved and grateful to get to the root of his problems, he decided to make this product available to everyone who needed to learn how to be confident.
Change Your Self-Image.
The product is called Quantum Confidence with the Morry Method, and it is one of a kind. You benefit from Morry’s unique expertise, and you can follow in his footsteps – to achieve the same results! If you are desperate to discover how to be confident, and you want to make a radical change in your life, then this system may be perfect for you. It doesn’t require any special skills, or a high level of dedication, as all you have to do is sit back and listen. So, why not do something to improve every area of your life today, and get your own copy now?
Reference: http://www.moreconfident.org/
I Want To Tell You, Mother
Even If,
We Are Not,
In The Same World,
But,
Mother,
I would like to inform you that your son is going to the next step with a wonderful result. Your son is going to the better way right now. Even if we are not staying closer each other but your son would like to say that he never forget what he told and promising with you at all, he is committing to achieve what he is planning and in order to make our family to be known around the country.
Your son is very quiet but what he does it is just trying to accomplish what he promised with you only. Keep quiet a little bit to commit to do a thing great!!!
Before die, at least I need 100,000,000 people around the world discuss and talk about me. this is very ambitious, isn't it?
By: Han4U
We Are Not,
In The Same World,
But,
Mother,
I would like to inform you that your son is going to the next step with a wonderful result. Your son is going to the better way right now. Even if we are not staying closer each other but your son would like to say that he never forget what he told and promising with you at all, he is committing to achieve what he is planning and in order to make our family to be known around the country.
Your son is very quiet but what he does it is just trying to accomplish what he promised with you only. Keep quiet a little bit to commit to do a thing great!!!
Before die, at least I need 100,000,000 people around the world discuss and talk about me. this is very ambitious, isn't it?
By: Han4U
Monday, July 16, 2012
Cannot Connect SQLServer 2008 with the provider SQLNCLI... Is there any SQL Server 2008 patch to support using SQLNCLI provider to access?
We have a program which developed under SQL Server 2005. In the
program the provider of the connect string is hard coded as "SQLNCLI".
It's ok running on SQL Server 2005. Now, for some reasons, this program
must run under SQL Server 2008 (x64). But our program
cannot access the SQL Server.
We check the reason, found that, in SQL Server 2008, SQLNCLI is changed to SQLNCLI10, this caused our program cannot run.
So I want to ask, is there any patch of SQL2008, so that the legacy program can normal access SQLserver with SQLNCLI WITHOUT rebuild a new version?
Answers:
Since SQLNCLI is published before SQL Server 2008 is published, it is designed to connect to SQL Server 7.0, 2000 and 2005. If we use this provide to connect to SQL Server 2008, it might work incorrectly. Therefore we recommend that you use SQLNCLI10 to connect to SQL Server 2008. Meanwhile SQLNCLI10 could also be used to connect to SQL Server 2005.
Reference: http://social.msdn.microsoft.com/Forums/eu/sqlexpress/thread/652549a7-f02c-4b9a-aab1-1686d303dc6c
We check the reason, found that, in SQL Server 2008, SQLNCLI is changed to SQLNCLI10, this caused our program cannot run.
So I want to ask, is there any patch of SQL2008, so that the legacy program can normal access SQLserver with SQLNCLI WITHOUT rebuild a new version?
Answers:
Since SQLNCLI is published before SQL Server 2008 is published, it is designed to connect to SQL Server 7.0, 2000 and 2005. If we use this provide to connect to SQL Server 2008, it might work incorrectly. Therefore we recommend that you use SQLNCLI10 to connect to SQL Server 2008. Meanwhile SQLNCLI10 could also be used to connect to SQL Server 2005.
Reference: http://social.msdn.microsoft.com/Forums/eu/sqlexpress/thread/652549a7-f02c-4b9a-aab1-1686d303dc6c
Friday, July 13, 2012
How to Become an Ethical Hacker
Not all hackers do evil work. Here's what you need to know to use your hacking skills to do good.
Do viruses, DDoS attacks, AspxSpy back dOOr or buffer overflows tickle your fancy? If so, you might consider becoming a legal hacker, aka an ethical hacker, "white hat" hacker, or penetration tester. Businesses and government-related organizations that are serious about
their network security hire ethical hackers and penetration testers to
help probe and improve their networks, applications, and other computer
systems with the ultimate goal of preventing data theft and fraud. You
may not get the same adrenaline rush that you might with underground
hacking, but you can earn a good and honest living--and not end up
facing prison time, as some illegal "black hat" hackers do.
Businesses and government-related organizations that are serious about
their network security hire ethical hackers and penetration testers to
help probe and improve their networks, applications, and other computer
systems with the ultimate goal of preventing data theft and fraud. You
may not get the same adrenaline rush that you might with underground
hacking, but you can earn a good and honest living--and not end up
facing prison time, as some illegal "black hat" hackers do.How does the job market look like for ethical hackers? Extremely good! The IT market overall continues to grow despite the current economic turmoil. Research firm Gartner estimates that worldwide enterprise IT spending grew by 5.9 percent between 2009 and 2010, to a total of $2.7 trillion. At the same time, security is becoming a more pressing concern. Gartner expects to see an increase of nearly 40 percent in spending on worldwide security services during the five-year period from 2011 to 2015, eventually surpassing $49.1 billion.
In your first years as an ethical hacker, you'll be in a position to earn anywhere from $50,000 to $100,000 per year, depending on the company that hires you, and on your IT experience and education. With several years of professional experience, you could command $120,000 or more per year, especially if you do your own independent consulting.
You can't just dive into an ethical hacker position, however. Without IT security experience, you won't get very far, even with degrees and certifications. As is true for other IT jobs, employers typically want candidates who have college degrees, but related experience is king. And experience with certifications can typically take the place of some degree requirements.
Getting Started
What you need to do to get started on the road to becoming an ethical hacker depends on where you are in the IT field. If you haven't started your IT career yet, you might even consider military service. The military offers many IT opportunities, and you get paid to go to school, even if you enlist in a part-time branch such as the National Guard or Reserves. Military service also looks good to employers that require security clearances.Start with the basics: Earn your A+ Certification and get a tech support position. After some experience and additional certification (Network+ or CCNA), move up to a network support or admin role, and then to network engineer after a few years. Next, put some time into earning security certifications (Security+, CISSP, or TICSA) and find an information security position. While you're there, try to concentrate on penetration testing--and get some experience with the tools of the trade. Then work toward the Certified Ethical Hacker (CEH) certification offered by the International Council of Electronic Commerce Consultants (EC-Council for short). At that point, you can start marketing yourself as an ethical hacker.
For a hacker, networking know-how is vital; but make sure that you gain experience in related areas as well. Discover and play with Unix/Linux commands and distributions. Make sure you also learn some programming--maybe C, LISP, Perl, or Java. And spend some time with databases such as SQL.
Soft Skills
Hacking isn't all technical. It also requires so-called soft skills, just as any other IT job does. You'll need a strong work ethic, very good problem-solving and communications skills, and the ability to say motivated and dedicated.Ethical hackers also need street smarts, people skills, and even some talent for manipulation, since at times they need to be able to persuade others to disclose credentials, restart or shut down systems, execute files, or otherwise knowingly or unknowingly help them achieve their ultimate goal. You'll need to master this aspect of the job, which people in the business sometimes call "social engineering," to become a well-rounded ethical hacker.
Stay Legal!
It's important never to engage in "black hat" hacking--that is, intruding or attacking anyone's network without their full permission. Engaging in illegal activities, even if it doesn't lead to a conviction, will likely kill your ethical hacking career. Many of the available jobs are with government-related organizations and require security clearances and polygraph testing. Even regular companies will perform at least a basic background check.Becoming a Certified Ethical Hacker (CEH)
As noted earlier, becoming a Certified Ethical Hacker (CEH) involves earning the appropriate credential from the EC-Council after a few years of security-related IT experience. The certification will help you understand security from the mindset of a hacker. You'll learn the common types of exploits, vulnerabilities, and countermeasures.Qualification for a CEH (a vendor-neutral certification) involves mastering penetration testing, footprinting and reconnaissance, and social engineering. The course of study covers creating Trojan horses, backdoors, viruses, and worms. It also covers denial of service (DoS) attacks, SQL injection, buffer overflow, session hijacking, and system hacking. You'll discover how to hijack Web servers and Web applications. You'll also find out how to scan and sniff networks, crack wireless encryption, and evade IDSs, firewalls, and honeypots.
Through approved EC-Council training partners, you can take a live, five-day onsite or online training course to prepare for the CEH cert. You can generally take live online classes over five consecutive days; onsite courses typically offer the content spread over a couple weeks for locals. In addition, you can take self-paced courses and work with self-study materials (including the CEH Certified Ethical Hacker Study Guide book) with or without the training courses. The EC-Council also offers iLabs, a subscription based-service that allows you to log on to virtualized remote machines to perform exercises.
The EC-Council usually requires that you have at least two years of information-security-related work experience (endorsed by your employer) in addition to passing the exam before it will award you the official CEH certification.
Resources
If you're interested in ethical hacking, you can consult many useful resources for more information. To start, check the resources section of the EC-Council site. A quick Amazon search will reveal many books on ethical hacking and the CEH certification, as well.With some googling, you can find simple hacking how-tos, which may motivate you even more. Consider downloading the Firefox add-on Firesheep or the Android app Droidsheep, and hijack your online accounts via Wi-Fi (but don't use these tools to hijack others' accounts--you could find yourself in legal trouble if you do).
Another option is to experiment with the BackTrack live CD. Try enabling WEP security on your wireless router at home, and then take a stab at cracking it. Check out Hack This Site to test and expand your skills. You could even set up a Linux box with Apache or buy a used Cisco router and see what you can do with it. If you want to play with malware, consider downloading--cautiously, and at your own risk--a malware DIY kit or a keylogger, and use it to experiment on a separate old PC or virtual machine.
Like other IT areas, hacking has conventions and conferences dedicated to it, such as DefCon, one of the oldest and largest of these. Such gatherings can be a great place to meet and network with peers and employers, and to discover more about hacking. DefCon also has affiliated local groups in select areas.
And remember, never attack or intrude on anyone else's network or computers without full written permission.
Eric Geier is the founder of NoWiresSecurity, which helps businesses easily protect their Wi-Fi networks with the Enterprise mode of WPA/WPA2 security by offering a hosted RADIUS/802.1X service. He is also a freelance tech writer—become a Twitter follower or use the RSS Feed to keep up with his writings.
Source: http://www.pcworld.com/article/250045/how_to_become_an_ethical_hacker.html
AspxSpy Back dOOr was found in my IIS server
Someone aimed to control and remote to my website in IIS webserver by using AspxSpy back dOOr file and fortunately I have found and deleted it on time successfully.
I found it on 13rd July 2012, the file is be able to control a whole compromised system either IIS or SQL server.
the AspxSpy back door authorized you can manage everything in the system, delete, remove, update and rename files as well.
That was very scared.
And now I am tracking all the files one by one to find whether where they are hiding it more.
Aspxspy is a Trojan horse ASP dot net script that provides an unauthorized remote user with access to a compromised IIS webserver.This tools allow hackers control over a compromised system.
Attacker can also use this attack to places web malware in infected website in fact they are of average size for a malware attacks of web applications.
By: Han4U
I found it on 13rd July 2012, the file is be able to control a whole compromised system either IIS or SQL server.
the AspxSpy back door authorized you can manage everything in the system, delete, remove, update and rename files as well.
That was very scared.
And now I am tracking all the files one by one to find whether where they are hiding it more.
Aspxspy is a Trojan horse ASP dot net script that provides an unauthorized remote user with access to a compromised IIS webserver.This tools allow hackers control over a compromised system.
Attacker can also use this attack to places web malware in infected website in fact they are of average size for a malware attacks of web applications.
By: Han4U
Thursday, July 12, 2012
SQL SERVER – How to Stop Growing Log File Too Big
I was recently engaged in Performance Tuning
Engagement in Singapore. The organization had a huge database and had
more than a million transactions every hour. During the assignment, I
noticed that they were truncating the transactions log. This really
alarmed me so I informed them this should not be continued anymore
because there’s really no need of truncating or shortening the database
log. The reason why they were truncating the database log was that it
was growing too big and they wanted to manage its large size. I provided
two different solutions for them. Now let’s venture more on these
solutions.
If you are jumping over this post to leave a comment, please read first the two options as follows:
1) Convert the Recovery Model to Simple Recovery
If you are truncating the transaction
logs, this means you are breaking the T-Log LSN (Log Sequence Numbers).
This follows that if disaster comes, you would not be able to restore
your T-Logs and there would be no option for you to do point in time
recovery. If you are fine with this situation and there is nothing to
worry, I suggest that you change your recovery model to Simple Recovery
Model. This way, you will not have extra ordinary growth of your log
file.
2) Start Taking Transaction Log Backup
If your business does not support loss of
data or requires having point in time recovery, you cannot afford
anything less than Full Recovery Model. In Full Recovery Model, your
transaction log will grow until you take a backup of it. You need to
take the T-Log Backup at a regular interval. This way, your log would
not grow beyond some limits. If you are taking an hourly T-Log backup,
your T-Log would grow until one hour but after this the T-Log backup
would truncate all the ‘committed’ transactions once you take it. Doing
this would lead the size of the T-Log not to go down much, but it would
rather be marked as empty for the next hour’s T-Log to populate.
With this method, you can restore your database at Point of Time if a disaster ever happens at your server.
Let us run an example to demonstrate this. In this case, I have done the following steps:
- Create Sample Database in FULL RECOVERY Model
- Take Full Backup (full backup is must for taking subsequent backup)
- Repeat Following Operation
- Take Log Backup
- Insert Some rows
- Check the size of Log File
- Clean Up
After a short while, you will notice that the Log file (ldf) will stop increasing but the size of the backup will increase.
If you have an issue with your log file
growth, I suggest that you follow either of the above solutions instead
of truncating it.
/* FULL Recovery and Log File Growth */
USE [master]
GO
-- Create Database SimpleTran
IF EXISTS (SELECT name FROM sys.databases WHERE name = N'SimpleTran')
BEGIN
ALTER DATABASE [SimpleTran] SET SINGLE_USER WITH ROLLBACK IMMEDIATE;
DROP DATABASE [SimpleTran]
END
GO
CREATE DATABASE [SimpleTran]
GO
-- Set Database backup model to FULL
ALTER DATABASE [SimpleTran] SET RECOVERY FULL
GO
BACKUP DATABASE [SimpleTran] TO DISK = N'D:\SimpleTran.bak' WITH NOFORMAT, NOINIT, NAME = N'SimpleTran-Full Database Backup', SKIP, NOREWIND, NOUNLOAD, STATS = 10
GO
-- Check Database Log File Size
SELECT DB_NAME(database_id) AS DatabaseName,
Name AS Logical_Name,
Physical_Name, (size*8)/1024 SizeMB
FROM sys.master_files
WHERE DB_NAME(database_id) = 'SimpleTran'
GO
-- Create Table in Database with Transaction
USE SimpleTran
GO
IF EXISTS (SELECT * FROM sys.objects WHERE OBJECT_ID = OBJECT_ID(N'[dbo].[RealTempTable]') AND TYPE IN (N'U'))
DROP TABLE [dbo].[RealTempTable]
GO
CREATE TABLE RealTempTable (ID INT)
INSERT INTO RealTempTable (ID)
SELECT TOP 50000 ROW_NUMBER() OVER (ORDER BY a.name) RowID
FROM sys.all_objects a
CROSS JOIN sys.all_objects b
GO
-- Check the size of the Database
SELECT DB_NAME(database_id) AS DatabaseName,
Name AS Logical_Name,
Physical_Name, (size*8)/1024 SizeMB
FROM sys.master_files
WHERE DB_NAME(database_id) = 'SimpleTran'
GO
-- Take Full Backup
BACKUP LOG [SimpleTran] TO DISK = N'D:\SimpleTran.bak' WITH NOFORMAT, NOINIT, NAME = N'SimpleTran-Transaction Log Backup', SKIP, NOREWIND, NOUNLOAD, STATS = 10
GO
-- Run following transaction multiple times and check the size of T-Log
INSERT INTO RealTempTable (ID)
SELECT TOP 50000 ROW_NUMBER() OVER (ORDER BY a.name) RowID
FROM sys.all_objects a
CROSS JOIN sys.all_objects b
GO
-- Check the size of the Database
SELECT DB_NAME(database_id) AS DatabaseName,
Name AS Logical_Name,
Physical_Name, (size*8)/1024 SizeMB
FROM sys.master_files
WHERE DB_NAME(database_id) = 'SimpleTran'
GO
/*
Now run following code multiple times.
You will notice that it will not increase the size of .ldf file but will for sure
increasethe size of the log backup.
*/
-- Second Time
-- START
BACKUP LOG [SimpleTran] TO DISK = N'D:\SimpleTran.log' WITH NOFORMAT, NOINIT, NAME = N'SimpleTran-Transaction Log Backup', SKIP, NOREWIND, NOUNLOAD, STATS = 10
GO
-- Run following transaction and check the size of T-Log
INSERT INTO RealTempTable (ID)
SELECT TOP 50000 ROW_NUMBER() OVER (ORDER BY a.name) RowID
FROM sys.all_objects a
CROSS JOIN sys.all_objects b
GO
-- Check the size of the Database
SELECT DB_NAME(database_id) AS DatabaseName,
Name AS Logical_Name,
Physical_Name, (size*8)/1024 SizeMB
FROM sys.master_files
WHERE DB_NAME(database_id) = 'SimpleTran'
GO
-- END
--Clean Up
USE MASTER
GO
IF EXISTS (SELECT name FROM sys.databases WHERE name = N'SimpleTran')
BEGIN
ALTER DATABASE [SimpleTran] SET SINGLE_USER WITH ROLLBACK IMMEDIATE;
DROP DATABASE [SimpleTran]
END
If you run the code that is listed between START and END, you would get the following results almost every time:

This validates our earlier discussion.
After seeing this article, the Singapore team implemented Log Backup
instead of Log Truncate right away. Let me know what you think about
this article.
Reference : Pinal Dave (http://blog.SQLAuthority.com)
Wednesday, July 11, 2012
The Best Strategy for Reducing Stress
Imagine you're sailing in the Bahamas, sipping a cold drink and listening to the water lapping the sides of the boat.
Relaxing, right? Not for my friend Rob.*
Rob is not usually stressed-out. For many people, Rob's daily work would be hair-pulling stressful — he's a real estate developer who routinely deals with a multitude of nagging problems related to renters, banks, lawsuits, property management, and rapidly changing valuations. But Rob routinely handles it all with steadiness and perspective.
So why was he stressed that blissful day on his boat? The same reason most of us get stressed: frustrated expectations. Rob had an important call to make and his cell phone wasn't working. He was experiencing the gap between what he expected to happen and what was actually happening.
That's the underlying cause of stress and it's afflicting us more these days than ever because our expectations keep rising, thanks in part to exponential improvements in our technology.
Full Article: http://blogs.hbr.org/bregman/2012/07/the-best-strategy-for-reducing.html
Relaxing, right? Not for my friend Rob.*
Rob is not usually stressed-out. For many people, Rob's daily work would be hair-pulling stressful — he's a real estate developer who routinely deals with a multitude of nagging problems related to renters, banks, lawsuits, property management, and rapidly changing valuations. But Rob routinely handles it all with steadiness and perspective.
So why was he stressed that blissful day on his boat? The same reason most of us get stressed: frustrated expectations. Rob had an important call to make and his cell phone wasn't working. He was experiencing the gap between what he expected to happen and what was actually happening.
That's the underlying cause of stress and it's afflicting us more these days than ever because our expectations keep rising, thanks in part to exponential improvements in our technology.
Full Article: http://blogs.hbr.org/bregman/2012/07/the-best-strategy-for-reducing.html
Less-Confident People Are More Successful
There is no bigger cliché in business psychology than the idea
that high self-confidence is key to career success. It is time to debunk
this myth. In fact, low self-confidence is more likely to make you successful.
After many years of researching and consulting on talent, I've come to the conclusion that self-confidence is only helpful when it's low. Sure, extremely low confidence is not helpful: it inhibits performance by inducing fear, worry, and stress, which may drive people to give up sooner or later. But just-low-enough confidence can help you recalibrate your goals so they are (a) more realistic and (b) attainable. Is that really a problem?
Not everyone can be CEO of Coca Cola or the next Steve Jobs.
If your confidence is low, rather than extremely low, you stand a better chance of succeeding than if you have high self-confidence. There are three main reasons for this:
It will motivate you to work hard, help you work on your limitations, and stop you from being a jerk, deluded, or both. It is therefore time debunk the myth: High self-confidence isn't a blessing, and low self-confidence is not a curse — in fact, it is the other way around.
Reference: http://blogs.hbr.org/cs/2012/07/less_confident_people_are_more_su.html?utm_source=feedburner&utm_medium=feed&utm_campaign=Feed%3A+harvardbusiness+%28HBR.org%29
By: Han4U
After many years of researching and consulting on talent, I've come to the conclusion that self-confidence is only helpful when it's low. Sure, extremely low confidence is not helpful: it inhibits performance by inducing fear, worry, and stress, which may drive people to give up sooner or later. But just-low-enough confidence can help you recalibrate your goals so they are (a) more realistic and (b) attainable. Is that really a problem?
Not everyone can be CEO of Coca Cola or the next Steve Jobs.
If your confidence is low, rather than extremely low, you stand a better chance of succeeding than if you have high self-confidence. There are three main reasons for this:
- Lower self-confidence makes you pay attention to negative feedback and be self-critical:
Most people get trapped in their optimistic biases, so they tend to
listen to positive feedback and ignore negative feedback. Although this
may help them come across as confident to others, in any area of
competence (e.g., education, business, sports or performing arts)
achievement is 10% performance and 90% preparation. Thus, the more aware
you are of your soft spots and weaknesses, the better prepared you will
be.
Low self-confidence may turn you into a pessimist, but when pessimism teams-up with ambition it often produces outstanding performance. To be the very best at anything, you will need to be your harshest critic, and that is almost impossible when your starting point is high self-confidence.
Exceptional achievers always experience low levels of confidence and self-confidence, but they train hard and practice continually until they reach an acceptable level of competence. Indeed, success is the best medicine for your insecurities.
- Lower self-confidence can motivate you to work harder and prepare more:
If you are serious about your goals, you will have more incentive to
work hard when you lack confidence in your abilities. In fact, low
confidence is only demotivating when you are not serious about your
goals.
Most people like the idea of being exceptional, but not enough to do what it takes to achieve it. Most people want to be slim, healthy, attractive and successful, but few people are willing to do what it takes to achieve it — which suggests that they don't really want these things as much as they think. As the legendary Paul Arden (ex creative director at Saatchi & Saatchi) noted: "I want means: if I want it enough I will get it. Getting what you want means making the decisions you need to make to get what you want.". If you really want what you say you want, then, your low confidence will only make you work harder to achieve it — because it will indicate a discrepancy between your desired goal and your current state. - Lower self-confidence reduces the chances of coming across as arrogant or being deluded.
Although we live in a world that worships those who worship themselves —
from Donald Trump to Lady Gaga to the latest reality TV "star" — the
consequences of hubris are now beyond debate.
According to Gallup, over 60% of employees either dislike or hate their jobs, and the most common reason is that they have narcissistic bosses. If managers were less arrogant, fewer employees would be spending their working hours on Facebook, productivity rates would go up, and turnover rates would go down.
Lower self-confidence reduces not only the chances of coming across as arrogant, but also of being deluded. Indeed, people with low self-confidence are more likely to admit their mistakes — instead of blaming others — and rarely take credit for others' accomplishments. This is arguably the most important benefit of low self-confidence because it points to the fact that low self-confidence can bring success, not just to individuals but also to organizations and society.
It will motivate you to work hard, help you work on your limitations, and stop you from being a jerk, deluded, or both. It is therefore time debunk the myth: High self-confidence isn't a blessing, and low self-confidence is not a curse — in fact, it is the other way around.
Reference: http://blogs.hbr.org/cs/2012/07/less_confident_people_are_more_su.html?utm_source=feedburner&utm_medium=feed&utm_campaign=Feed%3A+harvardbusiness+%28HBR.org%29
By: Han4U
Tuesday, July 10, 2012
Cambodia E-Visa Campaign 2012, Siem Reap Province
The season is coming,
E-visa is ready,
Siem Reap City, Land of Angkor Wat, Kingdom of Cambodia.
From 12nd until 14th July 2012, Cambodia e-Visa team will do a campaign to promote e-Visa to all tourists who are coming to visit the land of Angkor Wat. The campaign is yearly arranged in the half of every year. The year 2012 it is decided to do it on July 2012 because the high season is coming and that is expected that tourists will grow from this month onward.
We are delighted to announce to all hotels, airlines, travel agents and other resorts in Siem Reap province, please you kindly collaborate with us, accept us and allow the e-Visa leaflets or posters to be stuck in your places.
This is in a purpose of promoting the tourism industry to attract more tourists from over the world to visit Kingdom of Cambodia only.
The e-Visa system is getting more popular for the countries around the world, it is changing the way of how tourists apply for visa. With Cambodia e-Visa they can apply online in less than 10 minutes at anywhere and anytime from home, workplace or other locations that you are just required to have internet connection and computer only.
From now onward, you are no need to trip to Cambodia Embassy in your country to apply for it at all but you just go to http://mfaic.gov.kh/evisa/ platform to fill up application information and make payment by credit card online.
for more information please contact us at:
http://mfaic.gov.kh/evisa/Enquiry.aspx
Reference: http://cambodiaevisa.blogspot.com/2012/07/cambodia-e-visa-campaign-2012-siem-reap.html
E-visa is ready,
Siem Reap City, Land of Angkor Wat, Kingdom of Cambodia.
From 12nd until 14th July 2012, Cambodia e-Visa team will do a campaign to promote e-Visa to all tourists who are coming to visit the land of Angkor Wat. The campaign is yearly arranged in the half of every year. The year 2012 it is decided to do it on July 2012 because the high season is coming and that is expected that tourists will grow from this month onward.
We are delighted to announce to all hotels, airlines, travel agents and other resorts in Siem Reap province, please you kindly collaborate with us, accept us and allow the e-Visa leaflets or posters to be stuck in your places.
This is in a purpose of promoting the tourism industry to attract more tourists from over the world to visit Kingdom of Cambodia only.
The e-Visa system is getting more popular for the countries around the world, it is changing the way of how tourists apply for visa. With Cambodia e-Visa they can apply online in less than 10 minutes at anywhere and anytime from home, workplace or other locations that you are just required to have internet connection and computer only.
From now onward, you are no need to trip to Cambodia Embassy in your country to apply for it at all but you just go to http://mfaic.gov.kh/evisa/ platform to fill up application information and make payment by credit card online.
for more information please contact us at:
http://mfaic.gov.kh/evisa/Enquiry.aspx
Reference: http://cambodiaevisa.blogspot.com/2012/07/cambodia-e-visa-campaign-2012-siem-reap.html
Friday, July 6, 2012
SQL SERVER – Few Useful DateTime Functions to Find Specific Dates
Recently I have recieved email from Vivek Jamwal, which contains many useful SQL Server Date functions.
----Today
SELECT GETDATE() 'Today'
----Yesterday
SELECT DATEADD(d,-1,GETDATE()) 'Yesterday'
----First Day of Current Week
SELECT DATEADD(wk,DATEDIFF(wk,0,GETDATE()),0) 'First Day of Current Week'
----Last Day of Current Week
SELECT DATEADD(wk,DATEDIFF(wk,0,GETDATE()),6) 'Last Day of Current Week'
----First Day of Last Week
SELECT DATEADD(wk,DATEDIFF(wk,7,GETDATE()),0) 'First Day of Last Week'
----Last Day of Last Week
SELECT DATEADD(wk,DATEDIFF(wk,7,GETDATE()),6) 'Last Day of Last Week'
----First Day of Current Month
SELECT DATEADD(mm,DATEDIFF(mm,0,GETDATE()),0) 'First Day of Current Month'
----Last Day of Current Month
SELECT DATEADD(ms,- 3,DATEADD(mm,0,DATEADD(mm,DATEDIFF(mm,0,GETDATE())+1,0))) 'Last Day of Current Month'
----First Day of Last Month
SELECT DATEADD(mm,-1,DATEADD(mm,DATEDIFF(mm,0,GETDATE()),0)) 'First Day of Last Month'
----Last Day of Last Month
SELECT DATEADD(ms,-3,DATEADD(mm,0,DATEADD(mm,DATEDIFF(mm,0,GETDATE()),0))) 'Last Day of Last Month'
----First Day of Current Year
SELECT DATEADD(yy,DATEDIFF(yy,0,GETDATE()),0) 'First Day of Current Year'
----Last Day of Current Year
SELECT DATEADD(ms,-3,DATEADD(yy,0,DATEADD(yy,DATEDIFF(yy,0,GETDATE())+1,0))) 'Last Day of Current Year'
----First Day of Last Year
SELECT DATEADD(yy,-1,DATEADD(yy,DATEDIFF(yy,0,GETDATE()),0)) 'First Day of Last Year'
----Last Day of Last Year
SELECT DATEADD(ms,-3,DATEADD(yy,0,DATEADD(yy,DATEDIFF(yy,0,GETDATE()),0))) 'Last Day of Last Year'
ResultSet:
Today
———————–
2008-08-29 21:54:58.967
———————–
2008-08-29 21:54:58.967
Yesterday
———————–
2008-08-28 21:54:58.967
———————–
2008-08-28 21:54:58.967
First Day of Current Week
————————-
2008-08-25 00:00:00.000
————————-
2008-08-25 00:00:00.000
Last Day of Current Week
————————
2008-08-31 00:00:00.000
————————
2008-08-31 00:00:00.000
First Day of Last Week
———————–
2008-08-18 00:00:00.000
———————–
2008-08-18 00:00:00.000
Last Day of Last Week
———————–
2008-08-24 00:00:00.000
———————–
2008-08-24 00:00:00.000
First Day of Current Month
————————–
2008-08-01 00:00:00.000
————————–
2008-08-01 00:00:00.000
Last Day of Current Month
————————-
2008-08-31 23:59:59.997
————————-
2008-08-31 23:59:59.997
First Day of Last Month
———————–
2008-07-01 00:00:00.000
———————–
2008-07-01 00:00:00.000
Last Day of Last Month
———————–
2008-07-31 23:59:59.997
———————–
2008-07-31 23:59:59.997
First Day of Current Year
————————-
2008-01-01 00:00:00.000
————————-
2008-01-01 00:00:00.000
Last Day of Current Year
————————
2008-12-31 23:59:59.997
————————
2008-12-31 23:59:59.997
First Day of Last Year
———————–
2007-01-01 00:00:00.000
———————–
2007-01-01 00:00:00.000
Last Day of Last Year
———————–
2007-12-31 23:59:59.997
———————–
2007-12-31 23:59:59.997
Reference : Pinal Dave (http://blog.SQLAuthority.com), Vivek Jamwal
By: Han4U
Thursday, July 5, 2012
Cambodia E-Visa Galleries
 |
| AngkorWat Temples |
 |
| Preah Vihear Temples |
To see more Cambodia E-Visa galleries please click link below:
https://picasaweb.google.com/107288189848824308171
Wednesday, July 4, 2012
How to make your chairman smile and get your proposal approved
How To Get Your Project Approved
What do you do when you have a great idea? You know how to save your company a ton of money or you've thought of a way to really improve a product. The problem is that you know that you have a great idea, but no-one else does. And you can't convert this idea into reality by yourself. You need resources. You need money. You feel that you need permission. What do you do?If you're working for a large organisation there are probably written procedures for the analysis and approval of capital projects, but they are usually very generic and barren documents designed to handle a broad spectrum of projects. They don't tell you how to process your unique project and they say nothing about how to get approval for a non-capital project. You have to know how to move your idea through the bureaucratic machinery of the real world and convert it to a reality.
More detail: http://www.projectsmart.co.uk/how-to-get-your-project-approved.html
Tuesday, July 3, 2012
Looking for Cambodian programming expert
CINet Technologies Co,. Ltd is a professional and a local company in Cambodia which is developing and supporting the electronic visa system for the Ministry of Foreign Affairs. Furthermore CINet has been expanding one more business it is eCommerce system.
CINet is seeking for many experts, Cambodian only, who are professional in innovating of technologies, good at programming as well as analyzing the system.
Salary is not a problem, it is negotiable depend upon your experiences and educations.
No deadline. (be able to apply at anytime as you want.)
If you get this announcement, please do not hesitate to call or contact by 023 215 567, (working time: Monday - Friday)
Website: http://cinet.com.kh
Or send CV thru email address:
info@cinet.com.kh
CINet is seeking for many experts, Cambodian only, who are professional in innovating of technologies, good at programming as well as analyzing the system.
Salary is not a problem, it is negotiable depend upon your experiences and educations.
No deadline. (be able to apply at anytime as you want.)
If you get this announcement, please do not hesitate to call or contact by 023 215 567, (working time: Monday - Friday)
Website: http://cinet.com.kh
Or send CV thru email address:
info@cinet.com.kh
Subscribe to:
Posts (Atom)



